Get tailored blockchain and copyright Web3 articles sent to your application. Get paid copyright benefits by Understanding and finishing quizzes on how sure cryptocurrencies operate. Unlock the way forward for finance Using the copyright Web3 Wallet, your all-in-just one copyright wallet inside the copyright application.
Several argue that regulation efficient for securing banks is a lot less helpful from the copyright Room as a result of market?�s decentralized nature. copyright desires more stability rules, but Furthermore, it requirements new solutions that take into account its distinctions from fiat fiscal institutions.,??cybersecurity actions may come to be an afterthought, particularly when providers lack the resources or personnel for this sort of measures. The challenge isn?�t distinctive to Those people new to business; even so, even properly-set up businesses may Allow cybersecurity slide to the wayside or could absence the schooling to be familiar with the swiftly evolving menace landscape.
copyright.US will not be chargeable for any decline that you simply may possibly incur from selling price fluctuations whenever you obtain, provide, or keep cryptocurrencies. Make sure you confer with our Phrases of Use To learn more.
Obviously, This really is an extremely beneficial undertaking for the DPRK. In 2024, a senior Biden administration official voiced fears that all over 50% on the DPRK?�s international-forex earnings came from cybercrime, which incorporates its copyright theft actions, and also a UN report also shared promises from member states which the DPRK?�s weapons plan is largely funded by its cyber operations.
This incident is larger compared to the copyright market, and this kind of theft can be a subject of worldwide protection.
These danger actors had been then ready to steal AWS session tokens, the short term keys that allow you to ask for temporary credentials towards your employer?�s AWS account. By hijacking active tokens, the attackers ended up able to bypass MFA controls and gain use of Safe Wallet ?�s AWS account. By timing their attempts to coincide Using the developer?�s usual perform several more info hours, they also remained undetected until eventually the particular heist.
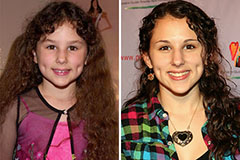 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Kirk Cameron Then & Now!
Kirk Cameron Then & Now! Andrea Barber Then & Now!
Andrea Barber Then & Now! Barbara Eden Then & Now!
Barbara Eden Then & Now! Naomi Grossman Then & Now!
Naomi Grossman Then & Now!